Solutions
Our Solutions
Our Solutions
Ventech Solutions provides products and services that enable government agencies and private sector companies to deliver IT services that are secure, efficient and effective. We have products and expertise that advance digital healthcare and remote monitoring to improve health outcomes and the quality of life for populations facing chronic and acute health challenges.

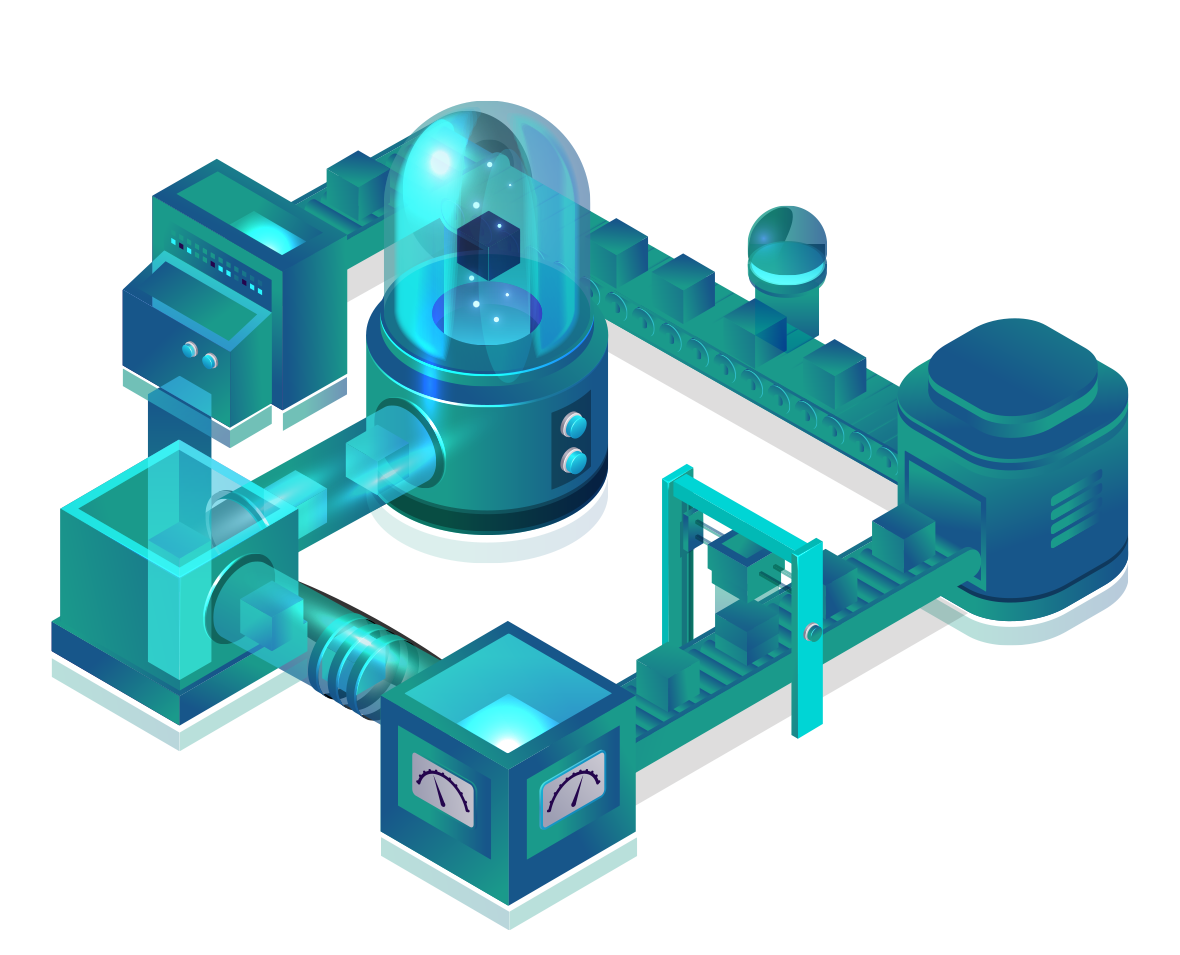
QurCLOUD is a highly secured cloud infrastructure environment for hosting clients’ sensitive data and applications. Built on the foundation of Amazon Web Services (AWS), the QurCLOUD environment ensures maximum cloud flexibility and increased compute, storage and cost efficiency.
QurCLOUD exceeds or meets all regulatory requirements and best practices including Healthcare Information Portability and Accessibility Act (HIPAA), Federal Information Security Management Act (FISMA), HITRUST, International Organization for Standardization (ISO), Capability Maturity Model Integration (CMMI) and the National Institute of Standards and Technology (NIST).
QurCloud Environment & Services
QurCloud provides a security, governance, and compliance wrapper for client applications and environments.

QurCloud provides a security, governance, and compliance wrapper for client applications and environments.

Qur Clients / Applications
QurHealth provides families and providers AI-powered digital healthcare information and remote monitoring capabilities.
Core QurCloud Services
- Security Operations Center (SOC)
- Antivirus & Vulnerability Scanning
- Security Information and Event Management
- Authentication and Remote Access
- Monitoring
- Valholla ™ - DevSecOps (CI/CD)
- Data Management
- Firewalls and Routing
- DNS
- Data Protection
*Note: QurCloud services are HITRUST Certified; however, we recommend that applications also undertake the certification process independently (Ventech offers expert support to achieve this goal).
QurProduct Compliance Vision
| Compliance with Frameworks | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|
Service Description |
FISMA | FDA 21 CFR 11 | HIPAA | Privacy Act | HITRUST | GDPR | ||||
QurCloud Shared ServicesCore cloud infrastructure services, Valholla cost management, governance, pipeline services |
||||||||||
QurCloud Shared ServicesCore cloud infrastructure services, Valholla cost management, governance, pipeline services |
Optional | Optional | Optional | Optional | Optional | Optional | ||||
QurCloud provides immediate General Support System (GSS) compliance assuring stakeholders of QurCloud customers commitment to the security of their offerings
Valholla | Integrated Into QurCloud
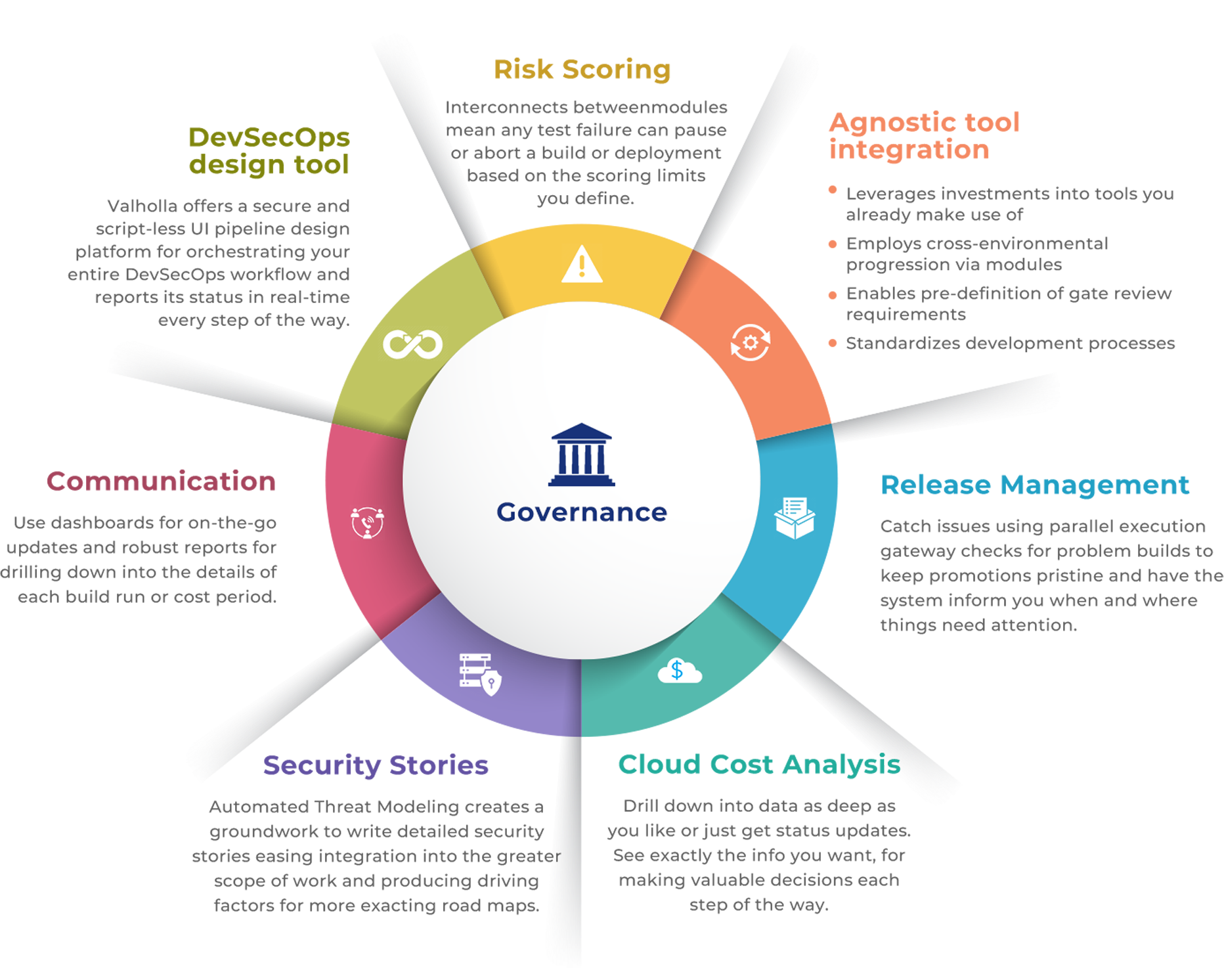

Valholla is an intelligent DevSecOps orchestration tool built to maximize Continuous Integration/Continuous Deployment (CI/CD) pipeline automation and cost efficiency through governance, continuous monitoring, cost management, and rapid touchpoint-free deployments. With Valholla, organizations can automate security compliance and functional testing reducing manually induced errors and ensuring adherence to standards. This automated security results in significant cost savings, substantial reduction in deployment time, enhanced risk mitigation and acceleration in incident responses. Government agencies, complex commercial enterprises and highly regulated industries leverage Valholla to become highly efficient, compliant and secure.
Valholla’s easy-to-deploy solution unifies existing DevSecOps tools and processes, thus leveraging the client’s existing IT investments. Highly configurable for organizations of all sizes and complexity, it provides real-time visibility for the Chief Information Officer (CIO), Chief Technical Officer (CTO), Chief Information Security Officer (CISO), Chief Risk Officer (CRO), Information System Security Officer (ISSO), developers, program managers and project managers.

The QurHealth suite of applications provide a digital health capability supported by an artificial intelligence (AI) powered conversational assistant that connects people to their families, providers and care coordination team with the rich array of information needed to improve care, outcomes and the quality of life. Our secure remote monitoring capabilities enable provider-tailored care plans, collect vital signs, collect patient reported symptoms, help ensure adherence to care activities and provide real-time alerts to all patient-consented parties when circumstances warrant.
Our digital technology provides support for Remote Therapeutic Monitoring (RTM) and Remote Physiologic Monitoring (RPM) for licensed clinicians enabling them to efficiently care for and guide people’s health while maintaining strict adherence to government and payer requirements for accurate reimbursement for services.
Our products run on QurCLOUD, a HITECH certified, FISMA, and HIPAA compliant infrastructure that is built and operated using the expertise that also operates Medicare’s quality measure processing systems, earning the highest security grades year over year from the government.
More details on QurHealth applications are available on the QurHealth website.

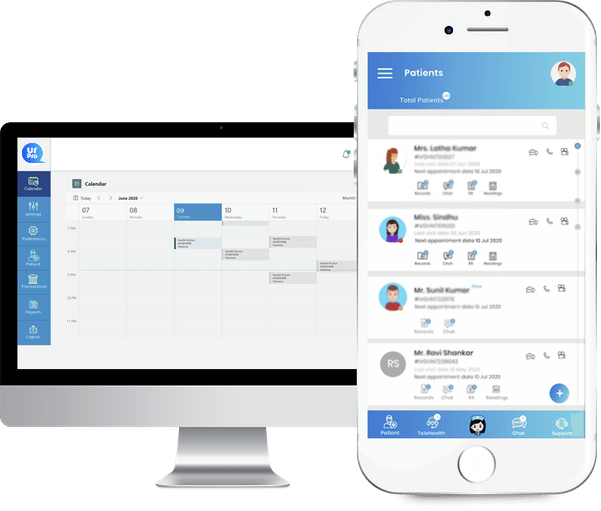



QurPro is a care provider-centric, 3 in 1 digital transformation solution designed for a hospital or clinic. The core of the solution is patient health records digitization and data exchange. Patients’ health records are scanned, saved, categorized and tagged. The Teleconsulting feature is simple, convenient, and appointment-driven, making a secure one-on-one connection with the patient to deliver a proactive and rich teleconsultation experience.

The patient engagement platform QurBook bridges a smart synergy between the doctor and the patient to access their health records and vitals to provide quality patient care.
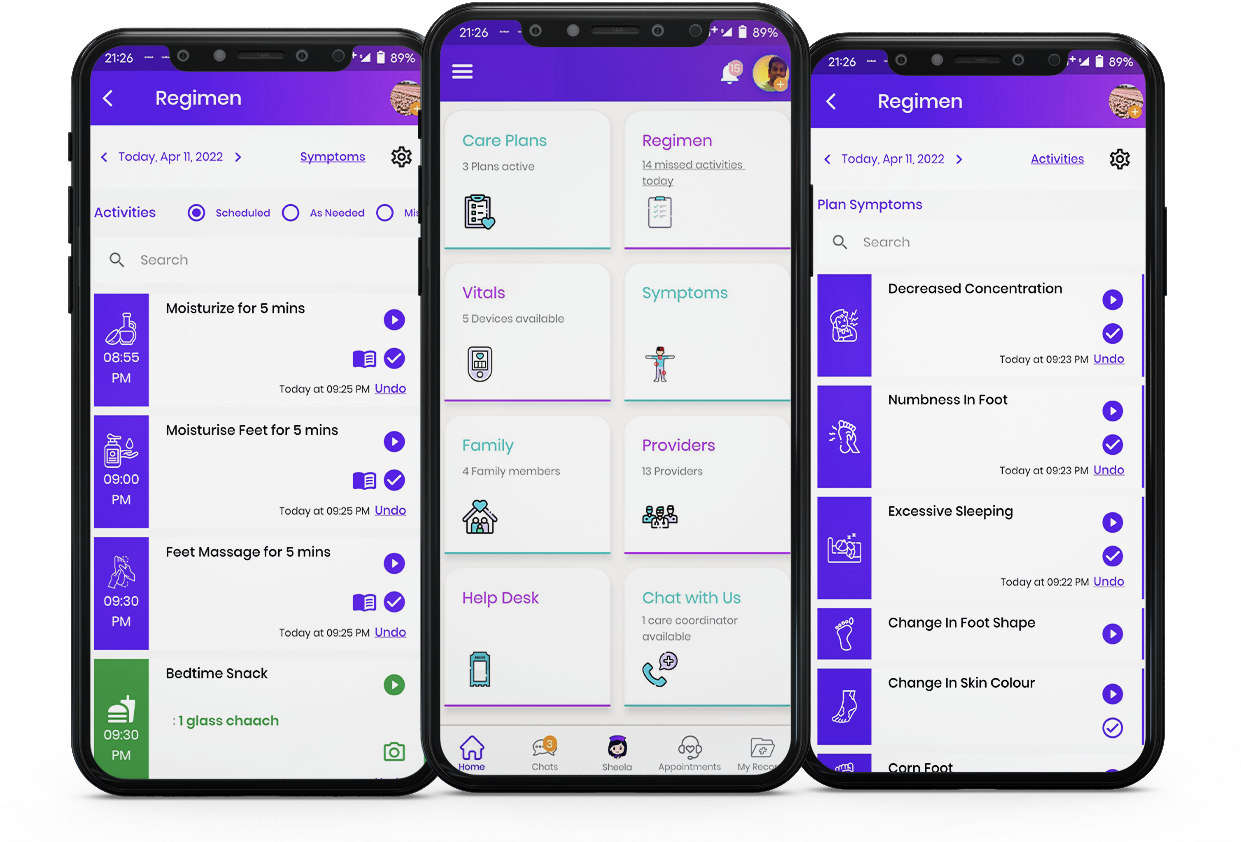


Sheela: AI-based Conversational Health Assistant!
Increased adoption of artificial intelligence in apps has opened up many real-life use cases to utilize voice commands for process automation.
QUR Suite is AI-powered and our healthcare voice assistant, Sheela, blends voice commands with AI skills. Just converse with Sheela and she can instantly facilitate access to your medical records and vitals as well as helping you manage appointments, create reminders and notifications, and much more.
Patient Profile
Device Reading
Appointment Management
Notifications
QUR Suite
QUR Suite is a clinical data exchange platform to connect payers, providers and patients. It's built with multi-layer stacked architecture and cutting-edge technology tools, deployed in a highly secured environment with a robust governance framework.
QurHealth aims to revolutionize patient-care delivery and create global health outcomes.
Ventech Solutions provides products and services that enable government agencies and private sector companies to deliver IT services that are secure, efficient and effective. We have products and expertise that advance digital healthcare and remote monitoring to improve health outcomes and the quality of life for populations facing chronic and acute health challenges.
Our Solutions
Ventech Solutions provides products and services that enable government agencies and private sector companies to deliver IT services that are secure, efficient and effective. We have products and expertise that advance digital healthcare and remote monitoring to improve health outcomes and the quality of life for populations facing chronic and acute health challenges.
QurData
At the heart of QurHealth is QurData, an intelligent platform that orchestrates the transformation of raw data into actionable healthcare intelligence performing deep-tech operations on de-identified data to deliver predictive outcomes. Through QurData, healthcare specialists can access critical patient insights for proactive care delivery. Researchers and scientists discover meaningful clinical patterns and actionable evidence that can speed up medical developments.
QurData leverages both QurCloud and Valholla capabilities, thereby ensuring DevSecOps governance benefits and fulfilling HIPAA and FISMA compliance requirements.


QurCLOUD is a highly secured cloud infrastructure environment for hosting clients’ sensitive data and applications. Built on the foundation of Amazon Web Services (AWS), the QurCLOUD environment ensures maximum cloud flexibility and increased compute, storage and cost efficiency.
QurCLOUD exceeds or meets all regulatory requirements and best practices including Healthcare Information Portability and Accessibility Act (HIPAA), Federal Information Security Management Act (FISMA), HITRUST, International Organization for Standardization (ISO), Capability Maturity Model Integration (CMMI) and the National Institute of Standards and Technology (NIST).
Learn more about how Ventech Solutions and AWS have collaborated to revolutionize patient-care delivery:
Driving Cloud Automation to Improve the Quality of Healthcare
Ventech Solutions engineers developed an AWS-centric automation strategy to accelerate development and reduce cloud maintenance costs.
QurCloud: A Healthcare Cloud Platform That Delivers
A premier software and systems solution company, Codice, hosts their flagship healthcare cost reporting application with QurCloud™, Ventech Solutions’ Security as a Service offering.

QurLake
QurHealth is firmly committed to advancing healthcare through data intelligence while protecting patient’s privacy. De-identification of the patient’s data is paramount and precedes the entire QurData conversion.
Designed specifically for use on structured healthcare data sets, QurLake’s de-identification engine performs two functions: De-identification of the data set (including both removal of patient information as well as modifications of patient information) and the insertion of encrypted patient tokens. The underlying technology is a cloud-based set of executables delivered as a solution to the AWS environment where data is being processed either at disparate data sources or centralized data aggregators and data users.